Now you are probably thinking that we have gone a bit loopy and are wondering why we are talking about the mythological Greek trojan horse right? Well while that would be impressive to fit that into a computer, we are actually referring to the type of malware that can encrypt a system and have a detrimental effect on your and your company’s data.
While we may have slightly touched on this topic as well as every other major type of hack that could cripple your system in our what is malware blog, we will be elaborating on each major aspect of malware in depth over various future blogs.
So, What Exactly Is The Trojan Virus?
A trojan is dangerous as it’s aim is to disguise itself as a normal file or program with the intention to trick users into downloading and installing it. Once this program has been downloaded and granted access into the system, the attacker will be given the autonomy to steal data, install further malware or even monitor all user activity. We cannot stress enough how vital it is to never download anything that looks even somewhat suspicious as downloading it yourself will bypass all security if you deem a program to be “safe” by your standards.
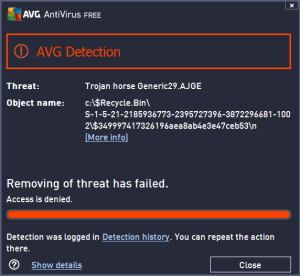
An generic example of this in action being detected you ask?
But How Can It Specifically Affect Me?
Trojan Viruses are versatile in their approach when it comes to the types of actions they can perform on your computer or overall network. Specifically, the malicious actions that can be evident include; deleting, blocking, modifying or copying data as well as of course disrupting the overall performance of any computer or network. While we have touched on how effective anti-virus programs when used can save a potentially detrimental situation, overall knowing how to prevent ransomware is the safest practice at any time through remaining educated on all matters, including Trojans.
Below are the 5 most common ways in which Trojan Viruses have affected devices in the past among our clients:
- Backdoor
- Perhaps the most common of all, this aspect of a Trojan allows the hacker to gain complete control over a specific device or network. Usually the malicious user will delete, modify and copy files as need be often resulting in illegal activities thus beginning to take place off of the system.
- Spy
- This is one of the most concerning types as once it has infected your system, the user is able to literally spy on how you are interacting with your computer. Any passwords you have used, usernames entered and screenshots of any visited websites can be obtained by the malicious hacker.
- Banker
- This Trojan is the quickest way for a hacker to wreak havoc on the victim. This Trojan as you may have guessed targets and account data on any website that is linked to a bank account of sorta. This can range from e payment “secure” checkouts, to Pay Pal, to your Westpac or Commonwealth Bank log in accounts.
- Downloader
- Once infected with this virus, the user will be able to download any malicious software onto your network or device in which any of these options could take place. This can even include any AdWare, Spyware or Spam as the hacker pleases.
- Ransom
- As aforementioned, ransomware is becoming an increasingly large epidemic Australia wide targeting both personal and company devices. This Trojan does target a device and as a result will modify the data within it so that either you can’t correctly use your device or can’t access the affected data.
Overall this type of virus can be prevented through installing effective anti-malware software which will protect a vast array of devices as well as being aware through our previous blog posts as to how to spot and detect any potential viruses.