Phishing: The attempt to acquire sensitive information such as usernames, passwords or credit card information often for unethical purposes by profiling itself as a “trusted” source.
It happens far too often to our service desk staff, calls from clients explaining that they have opened up “that” e-mail and now their whole system is down and as a result, the business is suffering…a virus is now spreading through the whole company’s IT system just because of one mistake. Unfortunately, every company is vulnerable to these attacks and in some rare cases, it will have to be dealt with swiftly and efficiently by your IT team no matter how preventative you are. While the thought of losing data and having the essence of your business go down due to an attack, the reality is that these types of situations can be avoided by following a few simple steps that can be implemented immediately on completion of reading this article.
So, take note, listen up and utilize this information to minimize risk to your IT systems as much as possible!
1: Are You Expecting An E-Mail From This Display Name?
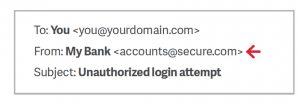
It sounds so simple doesn’t it? You wouldn’t think so but this is one of the biggest reasons for any viruses or attacks being able to enter a computer or network! Despite the fact that we get roughly between 50-100 e-mails per day on average, it is important to screen almost all of them as we can be lazy and open, delete or ignore any given e-mail that is evident within our inbox without thinking. As an example below, we can see that the domain name (secure.com) is not authentic with (mybank.com) which would be expected from the sender.
2: Don’t Open Any Attachments
In case you get lucky and do open an e-mail from an unreliable source without your system or network getting infected, certainly refrain from opening any attachments. Some fraudulent e-mails will send files, photos or any other type of attachment in order to “validate” their message. If you are unsure over the context and legitimacy of the e-mail, if there are multiple spelling and grammatical errors within the body of it then safe to say that it is unreliable and not from an official brand’s server.
3: Be Cautious Of Any Promotional E-Mails Coming From Government or Established Brands You Haven’t Subscribed To Receive
Following on from the previous statement to an extent, big brands and especially Government establishments are very serious about security, legitimacy and overall structure and grammar of their e-mails. Even if you don’t remember subscribing to some specific company blogs or services, you can gauge pretty well by the sender or profile that is piggybacking on a company’s name whether or not it sounds like something you would be interested in. If you take into consideration the previous two points and screen it further here, you should be able to get a pretty good indication whether or not it is legitimate.
4: Never Give Up Personal Information
Again, another simple one but if the company is in fact, “legitimate”, then it’s safe to assume that almost every big brand or bank will NEVER ask for personal information over e-mail. This will either be done through a phone call or in person if the situation or event calls for this action. If you ever happen to give out any information that can be used against you, then it could lead to a whole different can of worms for you and your company.
5: Authorization On Your Computer, Do You Reallllly Need Access To Everything?
One such way in which a network can get infected is through any profile that has unparalleled access to every bit of data and location on a server, virtual or physical. Realistically, SMB’s have no choice but to give almost all staff access to all data as it is instrumental to growth, however corporate companies can certainly protect large portions of their business if access is stripped back. Sit down with employees and different teams within the company to work out exactly what specific areas of a network and computer staff really need access to otherwise you run the risk of any employee opening a e-mail which could infect the whole system.
